Physical interface and cabling types is another topic from the current CCNA exam blueprint. Network engineers must know what the physical connectivity options exist, understand their limitations in speed and bandwidth. Power over Ethernet (PoE) is another related and important topic, as many critical devices are now dependent on network-delivered power. Network vendors and IEEE work to identify and standardize new ways to support higher power demands.
CCNA Exam test knowledge of these topics:
1.3 Compare physical interface and cabling types
1.3.a Single-mode fiber, multimode fiber, copper
1.3.b Connections (Ethernet shared media and point-to-point)
1.3.c Concepts of PoE
This first section is dedicated to types of physical interfaces available in Cisco LAN switches. The further sections present cabling and POE details.
Physical Interfaces
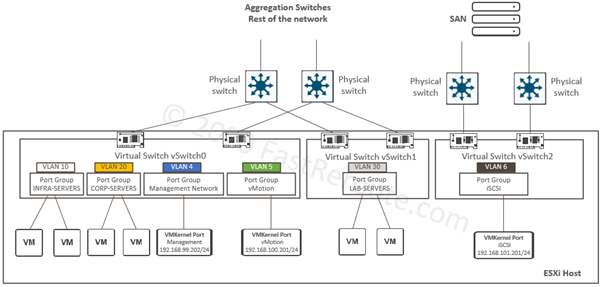
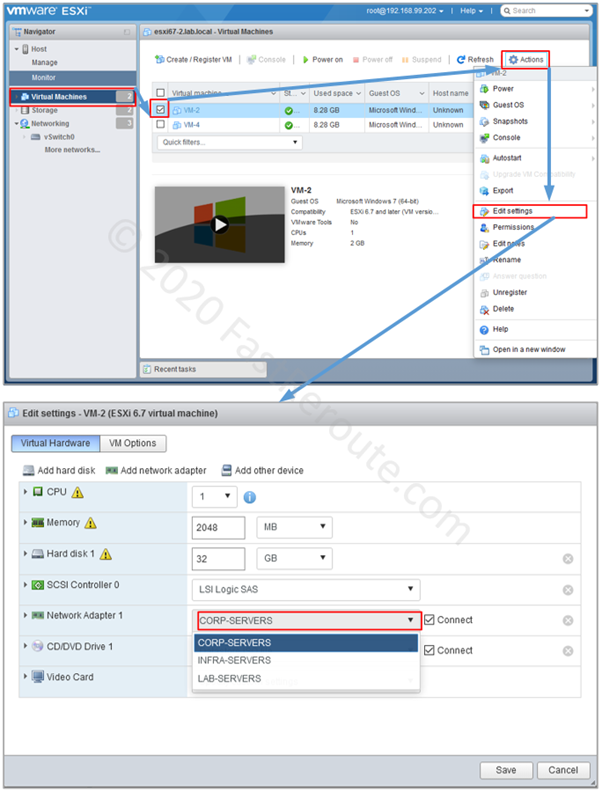
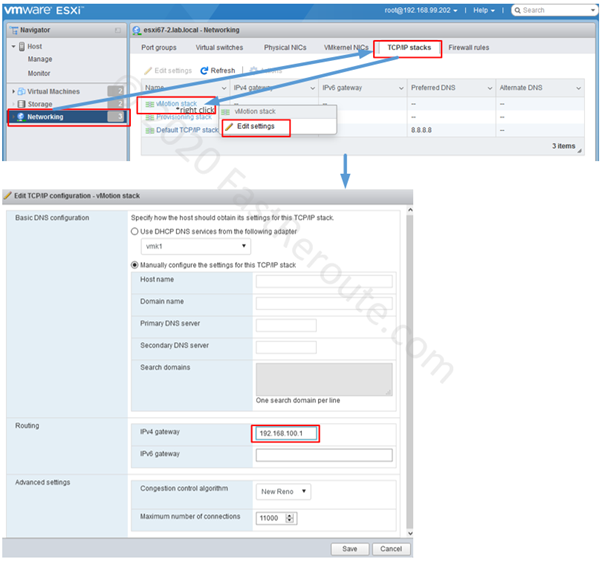
Cisco network devices can have either fixed ports or hot-pluggable transceivers slots. Figure 1 shows a Cisco Catalyst 9200 switch with 48x 10/100/1000 copper POE-enabled ports and an extension module, C9200-NM-4X which provides 4x SFP/SFP+ slots (on the right).

Courtesy of Cisco Systems, Inc. Unauthorized use not permitted
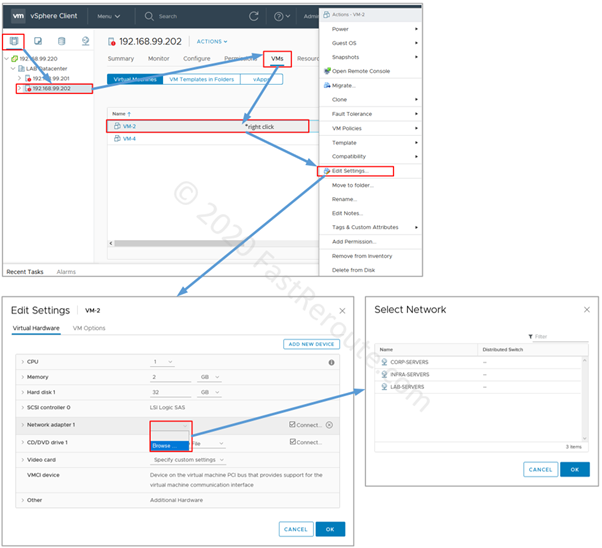
Different types of transceivers can be inserted into an SFP slot. For example, C9200-NM-4X module shown in Figure 1, can accept 1Gbps SFP modules and 10Gbps SFP+ modules. Figure 2 below shows SFP modules on the left and direct-attach Twinax copper cable on the right. This cable combines 2 connected SFPs and is a cost-effective way to connect devices in the same or adjacent racks.

Courtesy of Cisco Systems, Inc. Unauthorized use not permitted
Modern Catalyst switches, such as Catalyst 9000 series, have 2 types of copper interfaces:
- 10/100/1000Mbps
- Multigigabit with speed up to 10Gbps
Both types of interfaces support several standards and can negotiate different speeds with the connected device. For example, 10/100/1000 copper ports of Catalyst 9200 switch shown in Figure 1 support 10Base-T, 100-BaseTX and 1000Base-T. Multi-gigabit ports can negotiate 100Mbps, 1Gbps, 2.5Gbps, 5Gbps, and 10Gbps.
802.3 Standards
IEEE 802.3 family of standards defines physical interface specifications for the wired Ethernet. The table below shows some of the 802.3 standards.
| Standard | Specification | Physical Media |
|---|---|---|
| 802.3 | 10Base-T | UTP Cat 3 or higher |
| 802.3u | 100Base-TX | UTP Cat 5 or higher |
| 802.3ab | 1000Base-T | UTP Cat 5 or higher |
| 802.3z* | 1G over fiber | Different types of fiber |
| 802.3bz | Multirate 2.5G/5G | UTP Cat 5E or higher |
| 802.3an | 10G Base-T | UTP Cat 6 (55m), Cat 6A |
| 802.3ae** | 10G over fiber | Different types of fiber |
| 802.3by | 25Gbps | Different types of fiber, twinax |
| 802.3ba | 40Gbps/100Gbps | Different types of fiber, twinax |
Table 1. 802.3 Standards, Speed and Physical Media
*802.3z standard is called Ethernet over Fiber-Optic at 1Gbit/s and references multiple other standards. The example of commonly used options are 1000Base-SX (multi-mode fiber) and 1000Base-LX (multi-mode/single-mode fiber). Check this Wikipedia article for the full list.
**Has references to multiple standards depending on fiber type. The most commonly used options are 10GBase-SR, 10GBase-LR. Check this Wikipedia article for the full list.
Small Form-factor Pluggable Transceivers (SFPs)
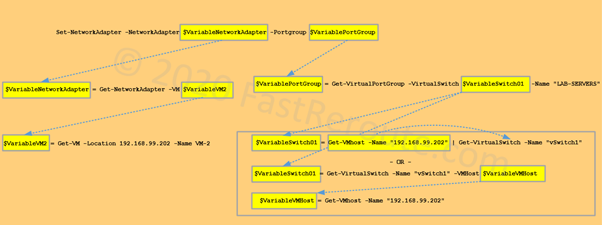
SFPs are network interface modules. Their specifications are developed and maintained by industry vendors group, i.e. not by IEEE. While the modules manufactured by different companies should be compatible, many vendors, including Cisco, support only their own branded SFPs. QSFP has a larger size and the picture below shows the difference between SFPs and QSFPs modules, as well as switch-side sockets. In this example, it is a Catalyst 9300 48-SFP+ port switch with a C9300-NM-2Q network module (accepting 2x QSFP+ modules).

Courtesy of Cisco Systems, Inc. Unauthorized use not permitted
The table below lists different types of SFPs along with the supported speed. To confirm if a specific module can be used in a specific Cisco device use the transceiver compatibility tool available here.
| Name | Speed |
|---|---|
| SFP | 1 Gbps |
| SFP+ | 10 Gbps |
| SFP28 | 25 Gbps |
| QSFP | 40 Gbps |
| QSFP28 | 40/100 Gbps |
| QSFP-DD | 100/400 Gbps |
Table 2. SFPs and Speed
Unshielded Twisted Pair
Copper connectivity is based on Unshielded Twisted Pair (UTP) cabling of different categories. A higher category number refers to the newer standard and better parameters. An Ethernet cable consists of 8 wires, which are twisted together in pairs. The maximum distance for copper cabling is 100m. The connector is called 8P8C and also commonly referred to as RJ45. There are 2 standards defining how individual wires are terminated within the connector – T568A and T568B. Refer to Wikipedia article for further information on pin-outs.
End devices have MDI (Medium Dependent Interfaces) ports and switches have MDI-X ports. -X means that the receive and transmit pairs are switched. To connect MDI to MDI-X straight-through cable is used. This cable has connectors with the same pin-out scheme used on both sides – either T568A or T568B. To connect MDI to MDI (host to host back-to-back), or MDI-X to MDI-X (switch to switch) crossover cable is required. A crossover cable has a connector with T568A pin-out on one side and T568B pin-out on another side.
Many modern switches can automatically switch their ports between MDI-X and MDI. They can use straight-through cables to connect to each other and don’t require a crossover cable.
Optical Fiber
Optical fiber cabling is usually more expensive to install, however, it has many benefits when compared to copper. In most cases, fiber cables can provide higher bandwidth over greater distances.
Fiber cabling is divided into 2 types:
- Multi-mode with categories of cables OM1, OM2, OM3, OM4 and OM5
- Single-mode of two types – OS1 and OS2
A fiber cable has a core and cladding around it. Multi-mode cable’s core is either 50 or 62.5 micrometers in diameter with 125 micrometers cladding. For comparison, human hair has a diameter between 20-40 micrometers. Single-mode cable’s core is thinner – between 8 and 10.5 micrometers in diameter with the same size 125 micrometers cladding. Multi-mode transmitters use a wavelength of 850nm and 1300nm; single-mode is 1310 or 1550 nm based. Cisco publishes information for each SFP on maximum supported distance based on cabling characteristics. These datasheets can be accessed via the Cisco transceiver compatibility tool. A very detailed comparison table of multimode cables is available here.
Single-mode cabling can cover much greater distances than multi-mode cables. See “Modal dispersion” article on Wikipedia explaining physics behind this.
Multimode OM numbers, as UTP categories, are better with larger number and provide better speed and distance. Single-mode OS1 is for indoor use/shorter distances and OS2 is for outdoor/long distance-use.
Connectors
Cisco fiber SFPs and some QSFPs have a duplex LC connector. Some QSFPs can also have MPO connectors. Check this article on Wikipedia with photos and specifications of different types of connectors.
Power Over Ethernet (POE)
Cisco Catalyst switches perform role of Power Sourcing Equipment (PSE). Cisco IP Phones, Access Points and other end devices are Powered Devices (PDs). Standards and data sheets usually list 2 power values:
- delivered on the switch port (PSE)
- received at the end device (PD)
The value at PD is always smaller than at PSE due to the power dissipation in cabling.
Standards
Cisco introduced its proprietary technology before IEEE standardized the POE. Cisco inline power can provide up to 10W at the PSE. Switch sends a fast link pulse to detect power enabled device, which then sends a link pulse back. The switch and device negotiate the final power level via Layer 2 capability exchange protocol – Cisco Discovery Protocol (CDP). Original Cisco inline power switches and end devices reached their End-Of-Support dates a long time ago and are replaced with newer platforms using POE standards described below.
In 2003 IEEE released the first POE standard – 802.3af. The standard isn’t compatible with Cisco’s proprietary implementation. PSE can deliver a maximum of 15.40W with available power at PD of 12.95W. This specification defined PD detection and classification mechanisms using electrical signaling. PD has an option to signal to the switch which class it belongs to. With this information, the switch knows how much power it should deliver. As table 3 shows, 802.3af defined 3 classes and class 0, which means that no classification is supported.
| Power (PSE side) | Specification | Class |
|---|---|---|
| 4W | IEEE 802.3af Type 1 | Class 1 |
| 7W | IEEE 802.3af Type 1 | Class 2 |
| 10W | Cisco inline-power | |
| 15.4W | IEEE 802.3af Type 1 | Class 3 |
| 15.4W | IEEE 802.3af Type 1 | Class 0 (not classified) |
| 30W | IEEE 802.3at Type 2 | Class 4 |
| 45W | IEEE 802.3bt Type 3 | Class 5 |
| 60W | IEEE 802.3bt Type 3 | Class 6 |
| 60W | Cisco UPOE | |
| 75W | IEEE 802.3bt Type 4 | Class 7 |
| 90W | IEEE 802.3bt Type 4 | Class 8 |
| 90W | Cisco UPOE+ |
Table 3. POE Wattage and Associated Standards
In 2009 IEEE released the new 802.3at standard. Devices supporting it were called Type 2 or POE+. PSEs and PDs complying with earlier 802.3af standard were labeled as Type 1 devices. 802.3at provides up to 30W/25.50W of power. Power levels of 30W and higher have additional stage negotiations using either electrical signals or layer 2 capability exchange protocols, such as LLDP and CDP.
Standard is backward compatible and supports 802.3af Class 1-3 devices. New Class 4 is allocated for 30W devices. 802.3at is widely used. Current generation of access switches, such as Catalyst 9200, and modern access points supporting it. Both 802.3af and 802.3at use only 2 pairs of wires in 4-pair UTP cable to provide power.
New use cases emerged, for example, smart buildings with POE-enabled lighting and network-powered display screens. These devices demanded more power. In 2011, Cisco introduced proprietary Universal Power over Ethernet (UPOE) technology to support up to 60W with the use of all 4 pairs in UTP cable. IEEE released 802.3bt standard in 2018 with up to 90W of power at PSE. The standard introduced Type 3 devices (60W) and Type 4 devices (90W). IEEE standard also made use of all 4.
Cisco UPOE and IEEE 802.bt Type 3 both deliver 60W but operate differently. Cisco publishes a list of UPOE Catalyst switches and line cards that comply with 802.3bt. Cisco proprietary UPOE+ was released to support 90W. UPOE+ switch modules can support 802.3bt Type 4 devices.
Some switches and line cards from Catalyst 9300 and 9400 families support UPOE and UPOE+. Catalyst 9200 switches support only POE+ (802.3at).