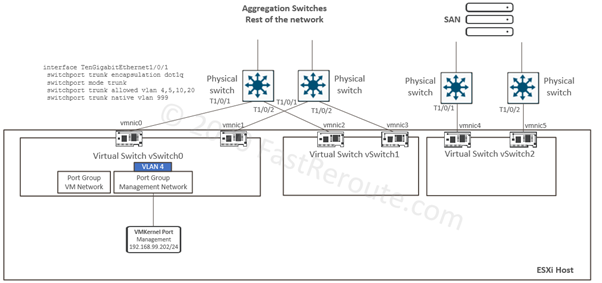
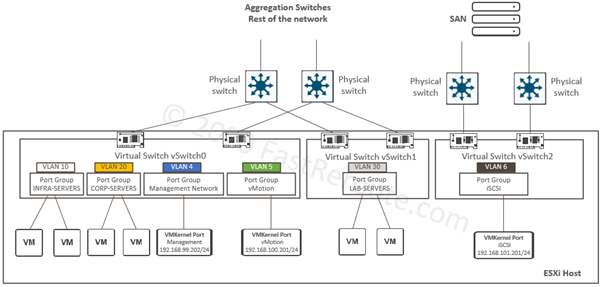
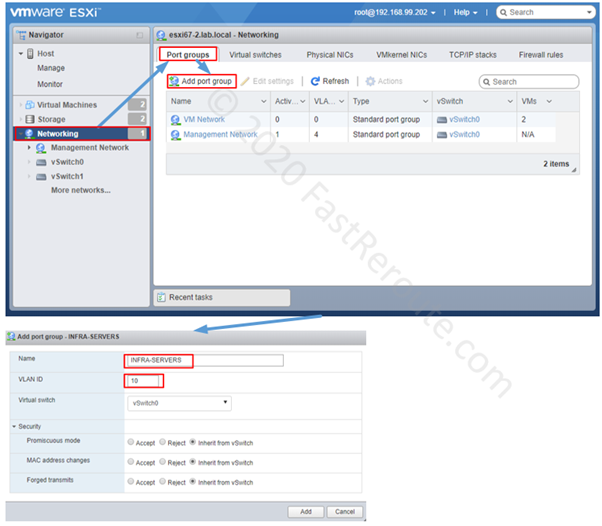
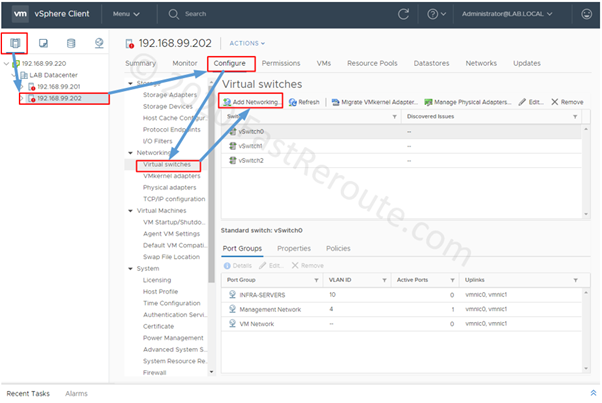
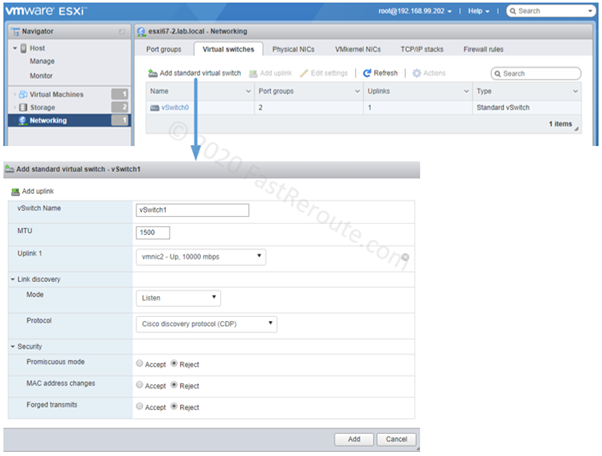
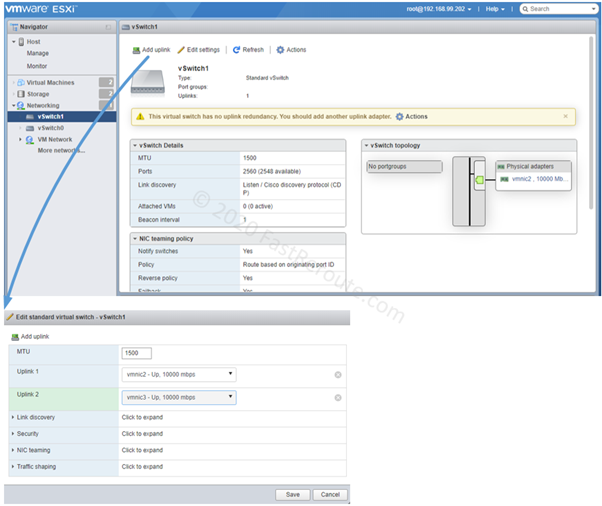
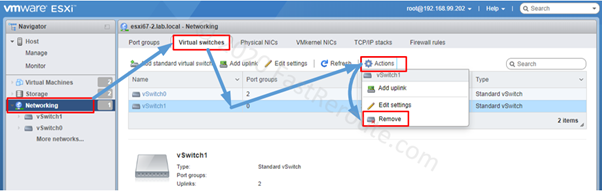
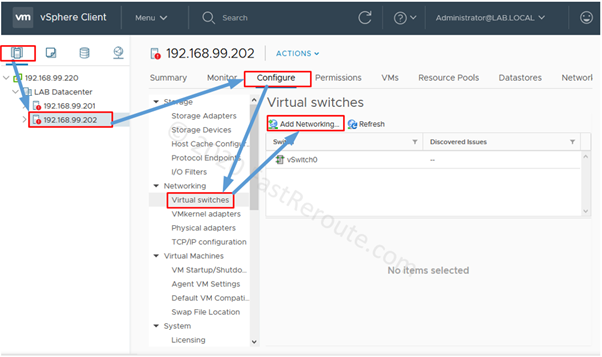
Editions and Packaging

vSphere 7 is available from April 2020. It is available in the same editions as vSphere 6.7 except for vSphere Platinum edition. As with vSphere 6.7, a support and subscription contract (SNS) is required. See our article on 6.7 editions here.
vSphere Standard and vSphere Enterprise Plus are the two main editions. Standard edition offers a base set of features, and Enterprise Plus extends the feature set with advanced capabilities.
VMware announced the end of availability (EOA) for vSphere Platinum Edition. AppDefense SAAS is now available as a standalone offering. See the details here.
vSphere 7 introduces add-on for Kubernetes, which allows deploying containerized applications. It is available as part of the VMware Cloud Foundation.
Licensing is CPU count-based. However, VMware had an update for the per-CPU pricing model in March 2020. After this update, CPUs with core count exceeding 32 require an additional license. Detailed information is available here.
As in previous editions, different types of packages and licensing types are available:
- vSphere Desktop. It can be used only for Virtual Desktop Infrastructure (VDI) deployments with either VMware Horizon View or third-party connection brokers.
- vSphere Acceleration Kits. These are bundles of vSphere licenses for 6 or 8 CPUs and a license for vCenter Server. The kits are convenience packages for purchasing. The actual licenses and software contracts can be used and renewed independently.
- vSphere Essentials Kits. These kits have enforceable limits of 3 hosts with 2 CPU each and a license for a single instance of vCenter Server for Essentials. In comparison to vSphere Acceleration Kits, Essentials Kits cannot be combined with other editions or decoupled.
- vSphere Remote Office Branch Office. This type of packaging limits the number of VMs available for deployment to 25 and targets remote branches.
- vSphere Scale-Out. This package is sold in packs of 8 CPUs for high-performance computing (HPC) and big data.
The following table lists feature set as available at the time of writing (June 2020). Check the following document for up-to-date information (URL).
Certain features may not be listed for specific packaging in VMware datasheets. To eliminate ambiguity, we’ve marked such features as “Not listed explicitly”.
| Feature | Essentials | Essentials Plus | ROBO Standard | ROBO Advanced | ROBO Enterprise | Scale-Out | Standard | Enterprise Plus |
|---|---|---|---|---|---|---|---|---|
| vSphere Hypervisor | • | • | • | • | • | • | • | • |
| vMotion | • | • | • | • | • | • | • | |
| VMware vCenter Hybrid Linked Mode | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | vCenter Server Standard | vCenter Server Standard |
| vSphere Virtual Symmetric Multiprocessing (SMP) | Not listed explicitly | Not listed explicitly | • | • | • | Not listed explicitly | • | • |
| vSphere High Availability (HA) | • | • | • | • | Not listed explicitly | • | • | |
| Storage vMotion | Not listed explicitly | Not listed explicitly | • | • | • | • | • | • |
| Fault Tolerance | Not listed explicitly | Not listed explicitly | 2 vCPU | 4 vCPU | 4 vCPU | Not listed explicitly | 2 vCPU | 8 vCPU |
| VMware vShield Endpoint | • | • | • | • | • | • | • | |
| vSphere Replication | • | • | • | • | Not listed explicitly | • | • | |
| Support for 4K native storage | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • |
| vSphere Quick Boot | • | • | • | • | • | • | • | |
| vCenter High Availability | vCenter Server Essentials | vCenter Server Essentials | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Standard | vCenter Server Standard | vCenter Server Standard |
| vCenter Backup and Restore | vCenter Server Essentials | vCenter Server Essentials | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Standard | vCenter Server Standard | vCenter Server Standard |
| vCenter Server Appliance Migration Tool | vCenter Server Essentials | vCenter Server Essentials | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Foundation | vCenter Server Standard | vCenter Server Standard | vCenter Server Standard |
| TPM 2.0 support and virtual TPM | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • |
| FIPS 140-2 compliance and TLS 1.2 support | • | • | • | • | • | • | • | |
| Support for Microsoft virtualization-based security (VBS) | • | • | • | • | • | • | • | |
| Per-VM Enhanced vMotion Compatibility | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • |
| VMware Instant Clone | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • |
| Identity federation with Active Directory Federation Services (ADFS) | Not listed explicitly | Not listed explicitly | • | • | • | • | • | • |
| Content Library | Not listed explicitly | Not listed explicitly | • | • | • | • | • | • |
| APIs for Storage Awareness | Not listed explicitly | Not listed explicitly | • | • | • | • | • | • |
| APIs for Array Integration, Multipathing | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • | • |
| Virtual Volumes and Storage-Policy Based Management | Not listed explicitly | Not listed explicitly | • | • | • | • | • | • |
| Next-generation infrastructure image management | • | • | • | • | • | • | • | |
| Cross-vCenter and Long Distance vMotion | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| VM encryption | Not listed explicitly | Not listed explicitly | • | Not listed explicitly | • | |||
| Distributed Switch | Not listed explicitly | Not listed explicitly | • | • | • | • | ||
| Host Profiles and Auto Deploy | Not listed explicitly | Not listed explicitly | • | • | • | • | ||
| Distributed Resource Scheduler (DRS) | Not listed explicitly | Not listed explicitly | • (limited) | Not listed explicitly | • | |||
| Distributed Power Management (DPM) | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Storage DRS | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| I/O Controls (Network and Storage) and SR-IOV | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | • | |
| vSphere Trust Authority | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| vSphere Persistent Memory | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| NVIDIA GRID vGPU | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Proactive HA | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Predictive DRS | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Accelerated graphics for VMs | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Dynamic vSphere DirectPath I/O™ | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| vCenter Server Profile | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | vCenter Server Standard | |
| vCenter Server update planner | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | • | |
| Bitfusion | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | Not listed explicitly | 2 GPU |
vCenter Server is available in 3 editions:
- vCenter Server for Essentials (up to 3 hosts; can manage only Essentials and Essentials Plus)
- vCenter Server Foundations (up to 4 hosts; can manage Standard, Enterprise Plus and vCloud Suite)
- vCenter Server Standard (unlimited hosts; can manage Standard, Enterprise Plus and vCloud Suite)
Feature and Scaling Comparison by Version
To check the full and the latest information, follow this URL.
| Feature | vSphere 6.5 | vSphere 6.7 | vSphere 7 |
|---|---|---|---|
| Kubernetes, VMware Tanzu Runtime and Hybrid Infrastructure Services | • (VMware Cloud Foundation) | ||
| vMotion (storage, cross-vSwitch, cross-vCenter, long-distance, cross-cloud hot and cold) | • | • | • |
| Content Library | • | • | • |
| Per-VM enhanced vMotion compatibility | • | • | |
| DRS, Storage DRS | • | • | • |
| Enhanced DRS | • | ||
| Network-aware DRS | • | • | |
| Network and Storage I/O Control | • | • | • |
| Assignable hardware support for vGPU and DirectPath I/O initial placement | • | ||
| Fault Tolerance | 4 vCPU | 8 vCPU | 8vCPU |
| Replication, HA VM component protection, Proactive HA, vCenter HA, Orchestrated HA Restart | • | • | • |
| Virtual Volumes, Storage Policy-based Management, NFS 4.1 Support, Automated UNMAP | • | • | • |
| Support for 4K native storage | • | • | |
| Multifactor Authentication, vSphere security hardening and compliance, VM encryption, Secure boot, Audit quality logging | • | • | • |
| TPM 2.0, virtual TPM 2.0, support for Microsoft VBS, FIPS 140-2 Validated | • | • | |
| vSphere Trust Authority, Identity federation with ADFS | • | ||
| VMware Instant Clone, NVIDIA vGPU | • | • | • |
| vSphere Integrated OpenStack, vSphere Integrated Containers | • | • | • |
| vMotion support for NVIDIA vGPU, vSphere Persistent Memory, support for memory mapping for 1GB page size | • | • | |
| Support for RoCE v2, iSCSI extension for RDMA (iSER), Support for RDMA InfiniBand | • | • | |
| vCenter Server Appliance, Certificate management, Migration to vCenter Server Appliance | • | • | • |
| Enhanced Linked Mode, vCenter Server Hybrid Linked Mode, vCenter Server backup and restore | • | • | • |
| HTML5-based vSphere Client, REST-based API for vCenter Server Management | • | • | • |
| Single reboot upgrades, vSphere Quick Boot, vCenter Server Appliance backup with built-in scheduler and retention | • | • | |
| vSphere Lifecycle Manager, vCenter Server update planner, vCenter Server Profiles | • |
Table 2. vSphere 6.5, 6.7 and 7.0 Feature Comparison
vSphere 7 supports a higher number of hosts per cluster and a higher number of hosts for linked vCenter servers. Table 3 captures scaling limits for different editions.
| Scale Metric | vSphere 6.5 | vSphere 6.7 | vSphere 7 |
|---|---|---|---|
| Hosts per cluster | 64 | 64 | 96 |
| VMs per cluster | 8,000 | 8,000 | 8,000 |
| Hosts per VMWare vCenter Server | 2,000 | 2,000 | 2,000 |
| Power-on VMs per vCenter Server | 25,000 | 25,000 | 30,000 |
| Hosts for 15 linked vCenter Servers | 5,000 | 5,000 | 15,000 |
| CPUs per host | 576 | 768 | 768 |
| RAM per host | 12TB | 16TB | 16TB |
| VMs per host | 1,024 | 1,024 | 1,024 |
| vCPUs per VM | 128 | 128 | 128 |
| vRAM per VM | 6TB | 6TB | 6TB |
| Non-volatile memory per host | 1TB | 1TB | |
| Non-volatile memory per VM | 1TB | 1TB |