This is the third article about the roles and functions of different network components (clock on the links for the first and second parts). In this part we will discuss operations of devices deployed on the network edge – Routers, Firewalls and Intrusion Protection Systems (IPSs).
Network edge provides connectivity between the company’s branch offices, data centers, remote workers, business partners, and the Internet. These devices must support a variety of transport technologies and provide security services.
There are two main types of edge connectivity:
- Internet
- WAN
Internet connectivity due to its public nature needs higher security control and devices such as firewalls, IPSs are usually deployed to enable the perimeter protection. Wide Area Network (WAN) in many environments was traditionally considered as a trusted network with only routers installed at the edge of each campus and branch.
In general, WAN links are more expensive and may not be available at every location. WAN connectivity is usually backed by agreed service level contracts and has guaranteed bandwidth and predictable latency. On the other hand, Internet links are cheap and offer more bandwidth, but no end-to-end service performance guarantees.
VPN tunneling over the Internet is used as a backup WAN connectivity method in many networks. Newer technologies, such as Cisco SD-WAN often use several Internet connections – as primary and backup WAN transport. SD-WAN routers can actively monitor links performance end-to-end and re-route traffic automatically based on the configured policy.
With these trends, the dividing line between WAN and Internet becomes less clear. Implementing security services on SD-WAN routers or installing firewalls behind it can be a reasonable choice.
Routers
The main function of a router is to perform Layer 3 forwarding or in most networks route IP (or IPv6) packets. Routers can run dynamic routing protocols to find the best paths to remote networks.
As we discussed in part 1 of this series, a Layer 3 Switch performs a similar function.
What is the difference between a Layer 3 switch and a router?
Historically, switches performed only Layer 2 functions and routers were responsible for Layer 3 operations. Topologies, such as router on a stick for inter-VLAN routing, were often deployed. Figure 1 displays a sample network demonstrating how the traffic between VLAN 10 and VLAN 20 hairpins via a router.
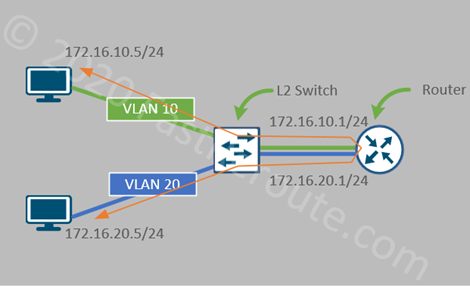
With the introduction of Layer 3 functionality in switches, inter-VLAN routing functionality was moved to them from routers. The term Layer 3 switching is used to describe fast, hardware-accelerated routing.
For example, aggregation-level router, such as Cisco ASR 1002-HX has a performance of up to 78Mpps, which is outperformed by the entry-level Catalyst C9200-24PXG access switch capable of switching up to 262 Mpps (million packets per second).
There is a balance between flexibility and performance. Routers are capable of providing more services and this is the reason they have lower layer 3 processing performance numbers. For example, routers support many types of WAN links (such as DSL variations and 4G LTE), can accept full Internet routing table, provide advanced QoS capability and application awareness, perform firewall zone-based services, establish VPN tunnels, act as voice gateways and many other features.
Cisco website has a tool called Feature Navigator that allows us to look up a feature that a specific platform or software version provides.
Cisco router product portfolio
Cisco routers can be grouped based on the type of location where they are typically deployed:
- Branch routers: ISR 900, ISR 1000, ISR 4000, Meraki MX
- WAN aggregation: ASR 1000, NCS 5000/5500
- Datacenter and clouds: CSR 1000v, Meraki vMX100
- Service provider routers: ASR 1000, ASR 9000, Cisco 8000 Series
Cisco router software
Previously, all enterprise Cisco routers were running the Cisco IOS software. It is now mostly replaced by IOS-XE. ISR 900 models are the only devices in the current product line that use IOS.
IOS-XE is IOS’s successor and the majority of enterprise-level devices, including ISR 1000, ISR 4000, ASR 1000 and CSR 1000v, are running it. IOS-XE is based on Linux kernel with IOS being a process called IOSd. IOS-XE and IOS share command-line syntax.
Enterprise platforms running IOS-XE can also run the SD-WAN version of the software, which allows the router to be managed by SD-WAN controllers (more information about SD-WAN platforms is available here).
Service provider routers, such as NCS 5000/5500 and ASR 9000 are running IOS XR software.
Firewalls and Intrusion Protection Systems (IPSs)
Let’s start this section by describing the logical functions of a firewall and an intrusion protection system.
Cisco firewall and IPS functions
A firewall evaluates traffic against configured ruleset and then allows or blocks it. A stateful firewall keeps track of allowed connections and can recognize return traffic, i.e. being part of an existing session, so it can be allowed too.
An Intrusion Protection System performs the security policy enforcement on transit traffic by either comparing its content to a set of patterns or by analyzing its behavior. These pre-defined patterns are called signatures and must be regularly updated.
Traditional firewalls and IPSs
Cisco product line used to have two different types of devices – one performing the firewall functions and another one was responsible for intrusion protection. Cisco PIX and its successor ASA (and routers with security feature set enabled) were performing traditional stateful firewall functions. They had some a limited IPS feature set too. However, for the full IDS/IPS functionality, Cisco IPS appliances and hardware modules were required. After SourceFire acquisition, its standalone IPS products were also added to Cisco’s product line.
Cisco provided integration options, however, they were based on two separately managed systems running in parallel. For example, ASA could accept an expansion module providing IPS functionality connected via ASA’s backplane. Later, hardware modules were replaced by virtual software processes using ASA as a host.
Next-Generation firewalls
Many security vendors took an approach of closely integrating both types of features in a single device, which became known as a Next-Generation Firewall (NGFW). Cisco also released a unified software platform that inherited ASA code as a stateful firewall engine and Snort IPS as intrusion protection system. This software is running on the current NGFW platforms and is called Firepower Threat Detection (or FTD).
In addition to stateful firewall and IPS functions, Next-generation firewalls can also provide remote and site-to-site VPN services, malware protection and URL filtering. The intelligence behind FTD NGFW services is provided by Cisco’s TALOS group that collects and analyzes threats to develop definition updates.
All FTD software platforms can be centrally controlled by Firepower Management Center. Smaller models can be configured locally with Web-based Firepower Device Management.
Cisco firewall and IPS product portfolio
Current Cisco’s firewall and IPS product portfolio includes:
- Firepower 1000/2100 (ASA or FTD image; locally or centrally managed)
- Firepower 4100/9000 (ASA or FTD image; only central management for FTD)
- Cisco NGFWv (virtual FTD – hypervisors and public clouds)
- Cisco ASAv (virtual ASA – hypervisors and public clouds)
- Cisco NGIPSv (for VMware)
- ASA 5500-X
- Meraki MX
Firewall deployment modes
Firewalls and IPSs are typically deployed on the network boundary with external networks, such as the Internet. Cisco NGFWs support 2 deployment modes:
- Routed
- Transparent
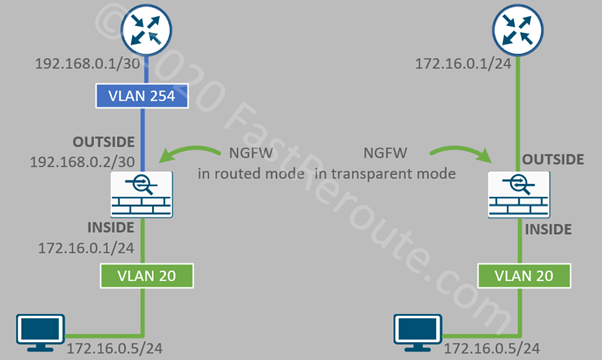
In routed mode, a firewall acts as a Layer 3 device, with each interface is assigned an IP address. Example in Figure 2 has NGFW in the routed mode option on the left. Notice that the workstation uses the INSIDE interface of the firewall as its default gateway.
On the right side, NGFW operates in transparent mode and performs the role of a Layer 2 device. It must be placed between the local network and the router, as there is no explicit configuration on the workstation, such as default gateway configuration to force the traffic to traverse the firewall.
The diagram shows that the transparent firewall is physically connected to the router ensuring that non-local traffic is not able to bypass the firewall.
In cases when such connectivity is not possible, so-called VLAN stitching can be used. To implement it, the connection between the router and the firewall external interface is allocated to different VLANs, which are stitched together by the firewall.