This blog post provides an overview of different network components and their role and functions. The article’s target audience is CCNA candidates and students looking for introductory information about computer network components. In this first post of the 3-article series, we will start by exploring the functions of endpoints and servers. Then the section about LAN switches will follow focusing on the difference between Layer 2 and Layer 3 switch operation.
Endpoints and Servers
The purpose of the infrastructure that the network devices create is to connect endpoints, such as computers, laptops, mobile and IP phones, and servers. A typical endpoint usually runs client applications, for example, a web browser and mail client that interact with the users. These network-enabled applications use services provided by network protocol stacks, drivers, and hardware components.
Out of all network components, endpoints have the most obvious role – they generate useful network payloads, such as digitized voice or Excel spreadsheets that are being transmitted over the network. And their function is to interact with a user, follow specific standards and protocols, so the transmitted data can be decoded on the receiving side of the connection.
Endpoints have an Operating System, which interacts with physical hardware using drivers. Operating System manages networking stack and provides APIs, so the application developers can work with the network without having to program low-level hardware components.
The most common type of wired connectivity is Ethernet, which is described by multiple IEEE 802.3 standards. Wireless communication is defined by IEEE 802.11 standards. Both types of connections use the same addressing, which is used to send frames between devices on the same network. Usually, this type of communication is referred to as Layers 1 and Layer 2 operations of the 7-layer OSI reference model. Layer 1 deals with physical specifications, such as electronic signals transferred over the wire. Layer 2 uses services provided by Layer 1 and is responsible for data framing and addressing.
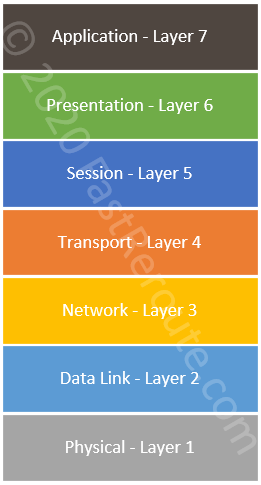
Almost all OS stacks support and prefer one of two versions of IP protocol (IPv4 or IPv6). Each endpoint is assigned with an IP address that is used for addressing when a packet needs to be transmitted over multiple physical networks. This type of communication is referred to as Layer 3 connectivity.
There are two IP protocols operating on Layer 4 – Transport Control Protocol (TCP) and User Datagram Protocol (UDP). A connection or flow between two devices is identified by source and destination port (both TCP and UDP use concept of ports). Connection is usually initiated by a client. Servers wait for new connections to be established by listening on a specific port. TCP port 0 to 1023 are well-known ports allocated to the specific applications. Client-side uses dynamically allocated ports.
Layer 2 Switches
CCNA blueprint doesn’t include Ethernet hubs, as there are now fully replaced by the switches. However, it is still helpful to understand the way a hub operates to understand the benefits that Layer 2 switches provide.
Early Ethernet network technologies were either bus or star topology-based. Bus topology would have end devices sequentially connected to each other with a coaxial cable. A hub allowed building a star-like topology where all UTP (twisted pair) cabling would terminate in a single location with the hub being the center of the star. In both cases, the network was shared medium and each machine must first listen if there is an active transmission on the network before sending any traffic on its own.
If 2 devices send traffic at the same time a collision occurs and both devices pause for some random amount of time before trying again. Such mode of operation is called CSMA/CD (Carrier-Sense Multiple Access with Collision Detection).
Hubs create a collision domain by re-sending traffic to every port except the ingress one, which makes total available bandwidth smaller as the number of devices increases.
Layer 2 switch solves the issue of sending traffic to all ports by inspecting incoming traffic and learning addresses of devices behind each port, so it can then send unicast traffic through the correct port, as opposed to flooding. BUM traffic (Broadcast, Unknown Unicast and Multicast) is still sent out of all ports. Switches also can store some amount of traffic in its buffers if there is more traffic to be sent than the port’s available bandwidth.
Endpoints connected to a switched port don’t need to listen if other hosts on the network are sending traffic and can send data at any time. Such ports are operating in full-duplex and will not experience collisions as the devices connected to hub ports.
Ethernet Layer 2 switches are usually placed at the access level with the end-users, phones, and printers connected to them. Most of the Cisco Ethernet switches have 24 or 48 ports.
In the topology shown below, the switch uses only hardware MAC address information to forward frames. Both PCs and servers will also have Layer 3 address, such as IP or IPv6, however, for a Layer 2 switch operation, this information is not being processed for traffic forwarding.
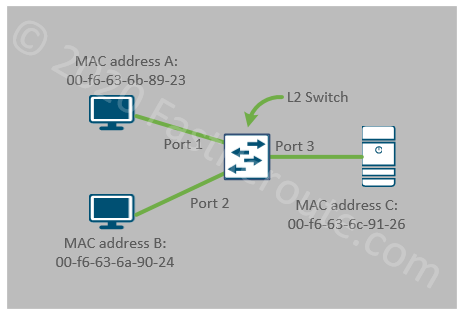
Layer 2 switches provide connectivity between hosts on Layer 2 with connected endpoints sharing the same broadcast domain and IP subnet. All 3 devices in the figure above are in the same VLAN and can communicate with each other. The switch will maintain a table of MAC address to port mappings.
Layer 2 switch can create broadcast domain boundaries by placing a group of ports into different VLANs, but it cannot provide communication between these domains. In the sample topology below A and B (ports 1 and 2) are in VLAN 10 and communicate with each other. C and D (ports 3 and 4) are in VLAN 20 and can also communicate with each other. There is no communication between VLAN 10 and VLAN 20 possible with only Layer 2 switch.
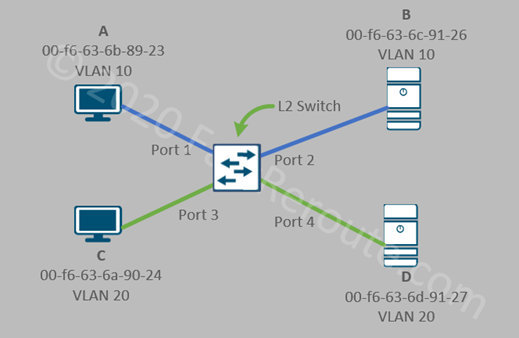
A layer 3 device is required to perform this function. In the campus network, it is the responsibility of a Layer 3 switches to provide connectivity between VLANs.
Layer 3 Switches
Layer 3 switches traditionally were placed at the distribution level, however, in modern networks routed access becomes more common. Almost all current Cisco switching platforms can perform inter-VLAN routing and can act as Layer 3 switches on the network. Therefore, the distinction between Layer 2 and Layer 3 switches is in their configuration, not the specific model.
Layer 3 switching is essentially IP routing or packet forwarding based on Layer 3 addressing. Modern Layer 3 switches perform routing in hardware and can provide very high throughput comparable to Layer 2 switching. However, Layer 3 switches have a smaller feature sets when comparing to routers, which can usually be found at the WAN edge of the network.
To perform its operation Layer 3 switch must have either a logical interface in VLANs that it routes for or a physical interface with IP address assigned to it.
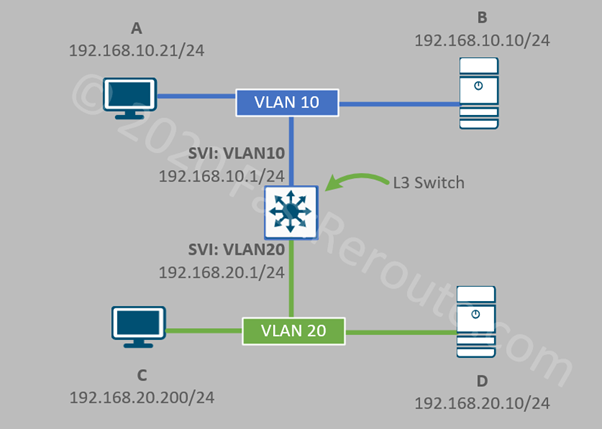
Switched Virtual Interface (SVI) is a logical interface named after VLAN it is connected to. It has an IP address allocated to it, to provide routing for this VLAN clients. As shown in the diagram below, Layer 3 switch has 2 SVIs – VLAN10 and VLAN20. Notice that now devices are shown with IPv4 addresses allocated to them instead of hardware MAC addresses, as this is the information relevant for Layer 3 switch operation.
Layer 2 operations are still performed in exactly the same way as described in the Layer 2 switch section. For example, if the workstation A sends a packet to the server B, no routing is required and Layer 2 forwarding is used to deliver the frame.
If host A will try to communicate to host D inter-VLAN routing will be performed by the switch, which will involve two-step process – Layer 2 communication between host A and switch VLAN 10 SVI; and another one between switch’s VLAN 20 SVI and the server D.
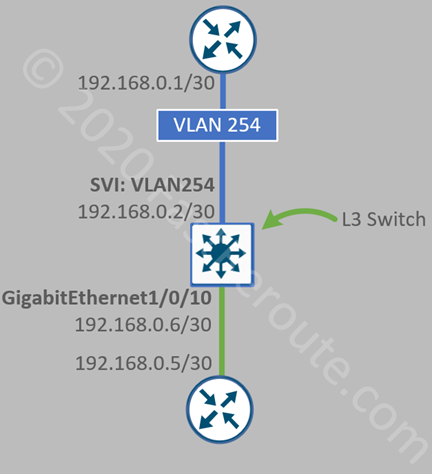
Physical IP interfaces are usually used on transit segments. Consider the topology shown in the next diagram. Switch connects to two routers. A point-to-point subnet of /30, which can accommodate only 2 hosts, has been to allocate to each of the connections. We now have two configuration options. The top router is connected via Layer 2 port which is a member of VLAN 254. We then create an SVI on the L3 switch for VLAN 254. As we assigned only a single Layer 2 port to this VLAN, the connection is point-to-point. This is similar to the previous example.
The second option is to configure the physical port, in our case, it is GigabitEthernet1/0/10 as Layer 3 port. We don’t have to consume a VLAN ID and configuration is contained within a single interface.
In the second part of these series of articles, we will discuss the operation of another type of LAN device which provides connectivity to the wireless clients – Access Points. Wireless LAN Controller functions will also be presented.
The third part of this series will be dedicated to devices that are usually found at the edge of the network, such as routers, firewalls, and IPSs.
DNA Center is introduced in its own article.