In this article, we introduce basic AWS Networking Concepts, such as Subnets, Route Tables, Elastic IPs, and Internet Gateways.
VPCs and CIDR Blocks
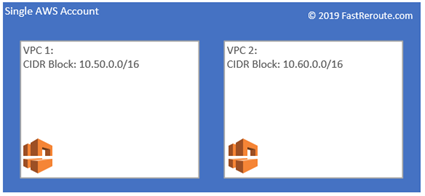
Virtual Private Cloud (VPC) is an isolated network within AWS that physically spans across all Availability Zones (AZ is a physical data center) in a region. A single AWS account can have several VPCs in the same or different regions.
VPC is assigned an IPv4 prefix (CIDR block) with the length between /16 and /28. Additional secondary IPv4 prefixes can be allocated if required.
There is no default communication between VPCs, even if they belong to the same account.
What is an AWS Subnet and a Route Table?
A subnet is a part of VPC’s IP CIDR block and has virtual machines or instance’s network interfaces attached to it. Subnet always belongs to a single availability zone.
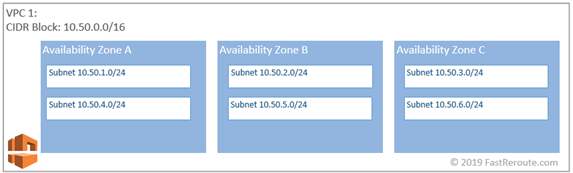
All subnets can communicate with each other directly within the VPC. Routing is done by implicit AWS VPC router, which is allocated the first IP address in each subnet’s range, for example, 10.50.1.1 for the first subnet in AZ A. Second IP address in each subnet is reserved for AWS DNS server, and third address is reserved for future use.
When you create a VPC, the main route table is created and all subnets are associated with it unless you override this configuration manually.
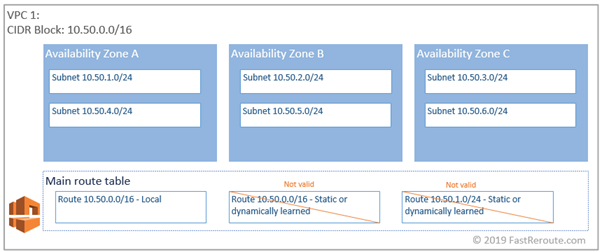
In the diagram below, you can see that the route table has a single route for VPC’s CIDR block 10.50.0.0/16, which is marked as local. Every route table will have this route automatically installed. The rule is that no route table within VPC can contain this route (or it is components, for example, 10.50.1.0/24) as propagated or statically configured. Therefore, don’t allocate IP prefixes from a VPC CIDR block outside of the VPC.
Local routes use implicit AWS VPC router, which is a virtual router that has an interface in every subnet and cannot be bypassed for subnet-to-subnet communication.
How routing works in AWS?
With the configuration performed so far, there is no connectivity outside of the VPC. There is a single route in the main routing table 10.50.0.0/16 that allows connectivity between subnets.
Traditional routing in IP is based on the ability to direct traffic to the next-hop router using the encapsulation appropriate for the link. In Ethernet, the MAC address of the next-hop router is carried in a frame and is resolved using a broadcast-based protocol ARP. AWS routing doesn’t work in the same way.
AWS doesn’t support broadcast (and multicast). Forwarding to the first hop (or default gateway) is not based on MAC address-based forwarding. To explain this concept, let’s launch 2 instances of Windows-based OS (any version will do). On the client VM (10.50.4.20) we will configure the default gateway of 10.50.4.10 (server virtual instance).
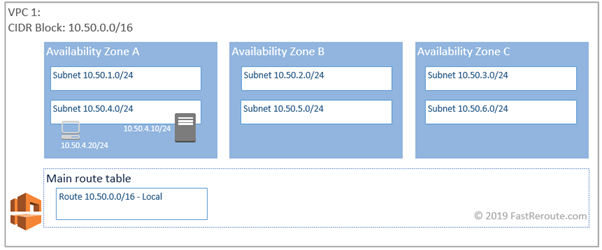
By default, the network adapter of an instance will not accept packets not destined to one of its addresses. To disable this behavior, Source/dest check set to false in network interface property of the server. Connectivity to external destinations outside of the VPC range is then tested by using tracert command. The expected behavior in traditional routing is for the first hop to reply, however, this didn’t happen.
In-instance routing if there are multiple interfaces only identifies the correct egress network adapter. Once the packet is transmitted and is on the subnet, the AWS route table is responsible for the forwarding. In our example, the default gateway can be configured to be any address on the 10.50.4.0/24 subnet.
What can be a next-hop for a route in the AWS route table?
In contrast to traditional routing – the IP address cannot be specified as the next hop. Available options are displayed in the screenshot below.
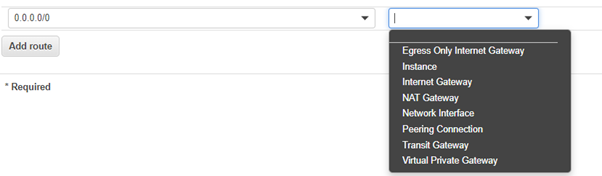
To fix the issue presented in the previous example we will select the network interface (or ENI) attached to the server instance using its resource ID. Now traceroute returns the correct first hop of 10.50.4.10.
The final configuration of route table is shown in the figure below.
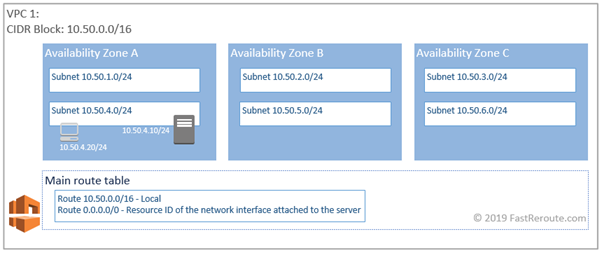
After introducing this default route, every virtual instance in every subnet within the VPC will be sending all it’s traffic to the server, as per the main routing table configuration. What if this behavior is not desired?
What is the use case for using additional AWS route tables?
A subnet can be associated with a single route table. If a specific subnet requires different forwarding compared to other subnets, a dedicated route table can be created and associated with this subnet. For the next example, we will remove the default route from the main route table, so no Internet access will be available from all subnets in the VPC. The web server in subnet 10.50.2.0/24, requires access to and from the Internet.
As this example is about routing, we assume that Internet Gateway and Elastic IPs and are pre-configured. These concepts will be covered later. For now, a new route table is created and the required subnet is explicitly associated with it. Then the default route with the next-hop of Internet Gateway (IGW) is configured. As a result, only 1 subnet will be able to communicate with the Internet.
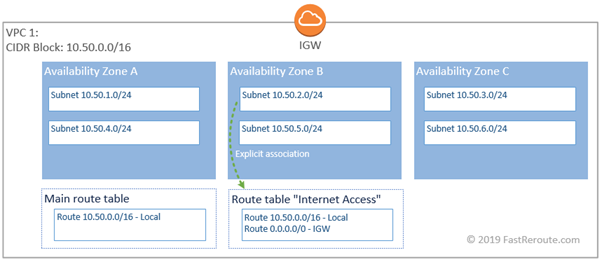
Internet Gateway and Elastic IPs
Internet Gateway (IGW) provides access to the Internet from VPC. It is attached to VPC and can be accessed from all subnets in VPC. It is a highly available component and AWS ensures that it is up even if one of the AZs fails. As shown in the previous section, to provide access to the Internet from a subnet, a default route is required which uses IGW as a default gateway.
The other requirement is publicly routed IP address. AWS performs NAT (Network Address Translation) and all hosts within the VPCs are using the private IP addresses. Publicly routed IP addresses are 1-to-1 mapped to an instance’s private IP address, as shown in the figure below. IGW is responsible for address translation.
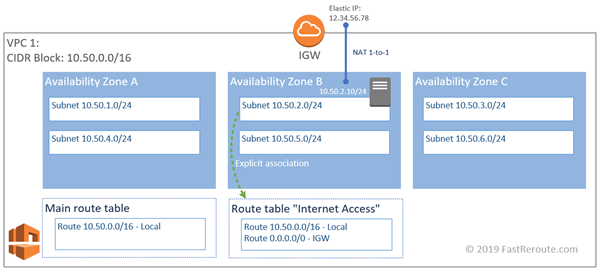
What is Elastic IP and how it is different to Public IP?
AWS Public IP can be assigned to your instance during provisioning. It maps to the primary IP address of the primary interface (eth0) of the instance. It is dynamic and is assigned from the AWS pool and will be returned back to the pool when an instance is powered off.
Elastic IP on the other hand is assigned to your account and will be reserved, even if the instance is powered off.
Is it possible to assign multiple publicly routable IP addresses to a single interface?
Yes, it is done by assigning several secondary private IP addresses to the network interface. Then each of the elastic IPs is associated with a secondary IP address.