The part 1 of this article (link) introduced basic AWS concepts, such as VPCs, subnets, route tables and Internet gateways. This post provides information on connectivity outside of a VPC.
VPC Peering
VPC peering establishes bidirectional connectivity between 2 VPCs. These VPCs can belong to different accounts and recently reside in different regions. CIDRs blocks of these VPCs must not overlap.
VPC peering is created by sending request from one of the VPCs and then accepting it from another. No gateway constructs are required to use VPC peering. Routes to remote side networks reference peering resource IDs, which use pcx- prefix. The following diagram shows VPC peering and associated routes for a sample topology.
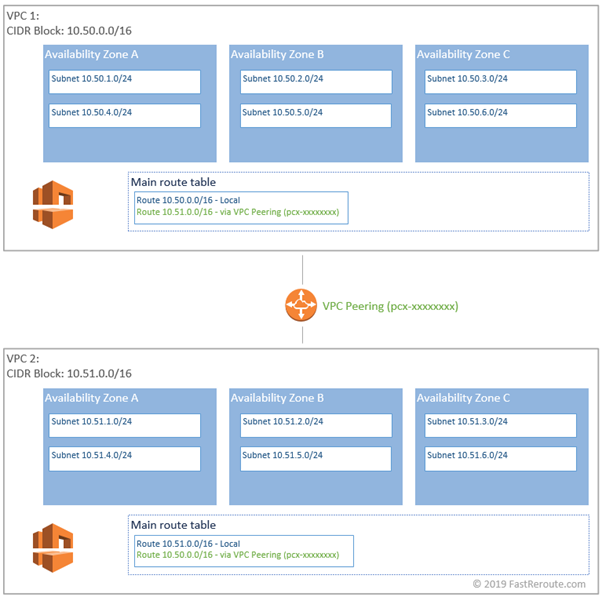
A VPC peering provides connectivity only between CIDRs in two VPCs. One peer cannot use another to transitively connect to other VPCs and external networks. For example, in hub-and-spoke topologies, spoke VPCs cannot communicate with each other by transiting hub over VPC peering. VPC cannot also access Internet Gateways, VPC endpoints, VPNs and Direct Connects of its peer.
Number of VPC peering connections is limited to 50 per VPC by default, with maximum of 125.
AWS VPNs
VPNs connects on-premises or partner networks to a VPC using AWS region-level construct called Virtual Private Gateway (VPG). High availability of VPN Connection is achieved by establishing 2 IPSec tunnels per connection.
VPN consists of 3 configuration elements:
- Virtual Private Gateway (uses prefix vgw-)
- Customer Gateway (prefix cgw-)
- VPN Connection
The diagram in Figure 2 shows a sample topology.
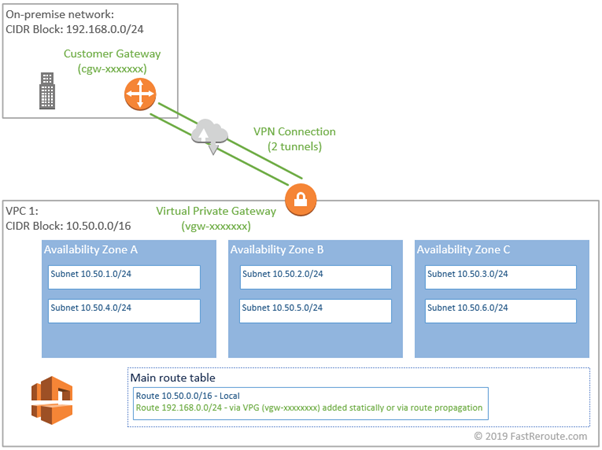
What is Virtual Private Gateway (VPG)?
In the context of VPN terminology, VPG is an AWS managed VPN concentrator. To gain connectivity to remote destination route tables use VPG as the target. An account can contain up to 5 VPGs per region and only one can be attached to a VPC at a time. You can allocate BGP AS Number to the VPG for dynamic routing. Otherwise, AWS will allocate ASN of 64512 automatically.
What is a Customer Gateway?
Customer Gateway is on remote side of the connection, for example, at the data center or on-premises network. Administrator creates Customer Gateway specifying its public IP address and type of routing (static or dynamic BGP).
VPN Connection
VPN connection uses VPG and Customer Gateway to create 2 IPSec tunnels. If connection is based on static routes you will require to specify IP network on Customer Gateway side. You can optionally designate point-to-point CIDRs for tunnel interfaces in 169.254.0.0/16 range and pre-shared keys at this stage.
Once connection is configured, you can download configuration files for your type of the device. This file will contain information on AWS side IP addresses, as well as pre-shared keys and encryption parameters.
AWS publishes sample configuration for different types of devices. For example, URLs below contain information on how to configure Cisco ASA firewall (with and without virtual tunnel interfaces):
https://docs.aws.amazon.com/vpc/latest/adminguide/Cisco_ASA.html
https://docs.aws.amazon.com/vpc/latest/adminguide/cisco-asa-vti-bgp.html
https://docs.aws.amazon.com/vpc/latest/adminguide/cisco-asa-vti-no-bgp.html
How to route traffic over VPN from a subnet?
Once tunnel is established and operational, VPG will update its routing table using BGP or static information you provided with remote subnet behind the Customer Gateway. However, VPC route tables by default don’t have this information. You can either add static routes to the required route tables or enable route propagation.
With route propagation VPG’s routes are automatically copied to the corresponding route table. The limit of propagated routes per route table is 100 and in many cases BGP route filtering and summarization should be done on the customer side.
AWS Direct Connect
Direct Connect is a dedicated private connection into AWS. Routers on AWS side are located in multiple locations around the world. There are 2 connectivity options.
First one is dedicated port on AWS side. This connection is Single Mode fiber-based and it is either 1000Base-LX (5 km maximum length) or 10GBase-LR (10 km) at the physical layer and 802.1q trunk on Layer-2. This option works if you require high throughput (LACP link aggregation is available) and your equipment is either collocated in a Direct Connect location or a service provider can extended it to your data center or office.
The second option is a hosted connection. In this scenario AWS Direct Connect partner makes its own dedicated connections available to multiple customers. A customer can obtain smaller bandwidth links compared to a dedicated port. Each hosted connection is allocated a 802.1q tag. To establish connectivity to multiple VPCs, you will need to obtain a hosted connection per VPC.
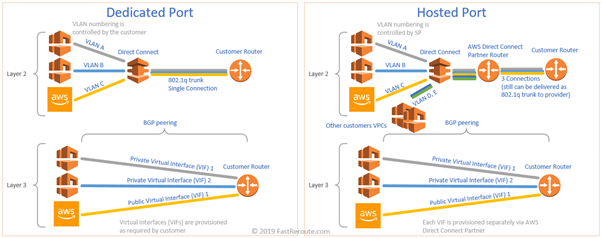
What is Virtual Interface?
Virtual Interface is a Layer 3 connection that is established over Direct Connect. With dedicated Direct Connect port, you can create multiple virtual interfaces. When hosted ports are in use, AWS Partner will provide a single Virtual Interface per connection.
Virtual Interface can be private or public. Private VIFs connect to VPCs and public VIF connects to AWS public services, such as EC2 and S3.
Virtual Interface must run BGP to exchange routes between VPC (or public AWS services) and customer network. Customer can use private BGP AS (Autonomous System) number, or, if available, it’s own public ASN. For public peering, list of public IP prefixes that will be advertised by the customer must be specified.
Where Direct Connect is terminated in VPC?
On AWS side Private Virtual Interfaces (VIFs) are terminated on Virtual Private Gateway (VPG) or VPC Direct Connect Gateway. Recently, VPC Transit Gateway has been announced and it is expected that it will be able to have Private VIFs terminated on it too.
VPC Direct Connect Gateway and Transit Gateways will be introduced in the next article.